Intune Device Migration
Migrations! From my experience, you simply cannot avoid a good old migration as a Technical Consultant. I remember the first one I did - a fresh faced 18 year old manually exporting and importing Outlook PST files into a new Hosted Exchange Provider - yeah the thought of that makes me cringe now too!
But we've come along way since then, from carrying out many Windows Server, Desktop, Exchange, SharePoint and even a couple of Teams Telephony migrations! Now these days, it's mainly M365 tenant to tenant migrations I see and once you have yourself a solid scope of what is and isn't included, the art of migrating data and configuration settings isn't too bad - at least you can do it from home and not in a chilly server room 😁
Device Migration challenges
Although we can't forget about the end users and their devices can we?! This becomes the added layer of complexity when running these migration as a home working consultant. As with an Intune enrolled and Entra Joined device, your typical approach is a device reset and Autopilot enrolment into the destination.
Now with 50 users, not too bad - I did a brilliant project with a fantastic Project Manager (BC Migration - you know who you are if you read this!) who managed all the end user comms and politics - while I focused on the process and guidance for users to run the resets themselves. It worked great, but there was a lot of jumping between tenants until all the data was cut-over.
Now what about 500 users with a domain cut-over - that's more of an issue, logistically you need a project team with boots on the ground to manage these device resets and ensure users are happy. Plus, when you're consulting, the customer is going to have to pay for that time and additional resource.
The Intune Device Migration Solution
Now, this is where we are graced by some extremely intelligent and determined people in the Microsoft Intune community, Steve Weiner from GetRubix.com has developed a fantastic solution, which solves this headache and I've had success using this for a tenant migration recently. So let's have a look (of course we'll have a look - I really hope someone get's that reference 😄)

The migration solution can migrate a device between Entra and Intune tenants and also can do a Hybrid join device to Entra Joined device - great when decommissioning your Active Directory. Go ahead and check-out Steve's in depth documentation linked above, which also serves as a great learning tool to understand the mechanics of how Entra Join and Intune enrolment work on the device side.
I've tested this many times now and have had success with both the Hybrid and tenant migration scenario, I'll briefly go through the steps required for the tenant migration scenario below, please refer the guide here for the full requirements - https://stevecapacity.github.io/intune-device-migration-documentation/pages/deploy/
Walkthrough
The purpose of my walkthrough is to show you what you will have configured and any pointers I found which were useful during testing and the live deployment, don't rely on this to deploy the solution I am simply spreading the word and giving my own perspective 🤘
Downloads
1) Download the solution here - https://github.com/stevecapacity/intune-device-migration-8
2) Download Visual Studio Code here - https://code.visualstudio.com/
3) Download Windows Configuration Designer here - https://apps.microsoft.com/detail/9nblggh4tx22?ocid=pdpshare&hl=en-us&gl=US
4) Download the Intune Content Prep Tool here - https://github.com/microsoft/Microsoft-Win32-Content-Prep-Tool
App Registrations
5) Create your Migration App Registrations in both the source and destination tenants, you'll be adding the below Graph Permissions and granting admin consent for the magic to happen:
Device.ReadWrite.All
DeviceManagementManagedDevices.ReadWrite.All
DeviceManagementServiceConfig.ReadWrite.All
User.Read.All
Next, create your secret and make a copy of that, plus the Client ID for the next steps!
Visual Studio Code - config.json
6) Launch Visual Studio Code from the directory where you have saved the migration solution, which should now take you to this view:
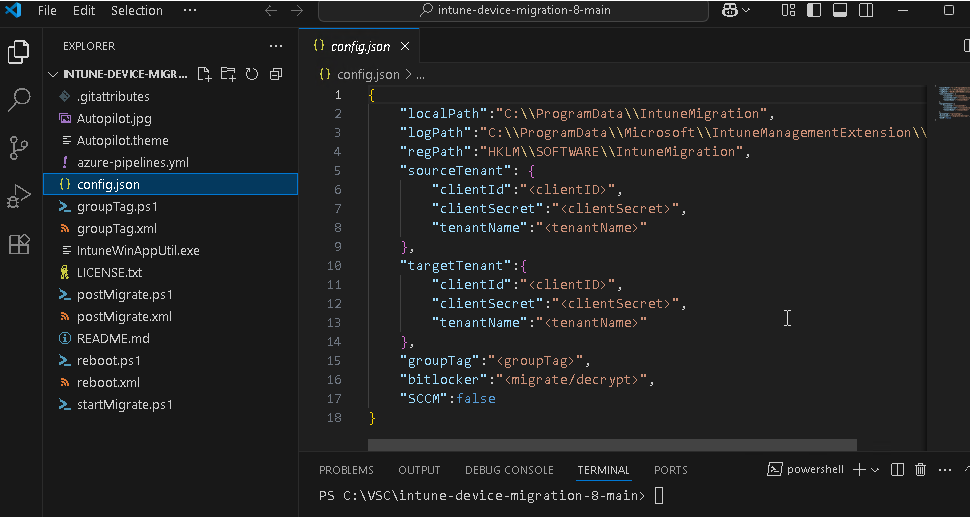
Input the details from the previous step for the clientId and clientSecret values for both the source and destination - make sure they're correct - or you're device may end up in no mans land 😀 - this obviously never happened to me and I always test with a VM anyway ;)
7) Input your tenantName, for testing you can use the .onmicrosoft.com domains and it will work. But in the real world input the correct domains that are in use as the user will see a message saying they have been migrated to "yourdomain.com".
8) For groupTag, I have been able to leave this blank for testing but input whatever you have configured in your environment.
9) For bitLocker, you can choose to decrypt or migrate - we used migrate in the tenant migration. For my VM testing, I had no BitLocker so you can leave that option blank and it will work.
10) For SCCM, I've left that as false as not in use.
Bulk Enrolment Token - Windows Configuration Designer
This was an interesting one for me, I never actually knew about this tool before looking at this solution - always learning!
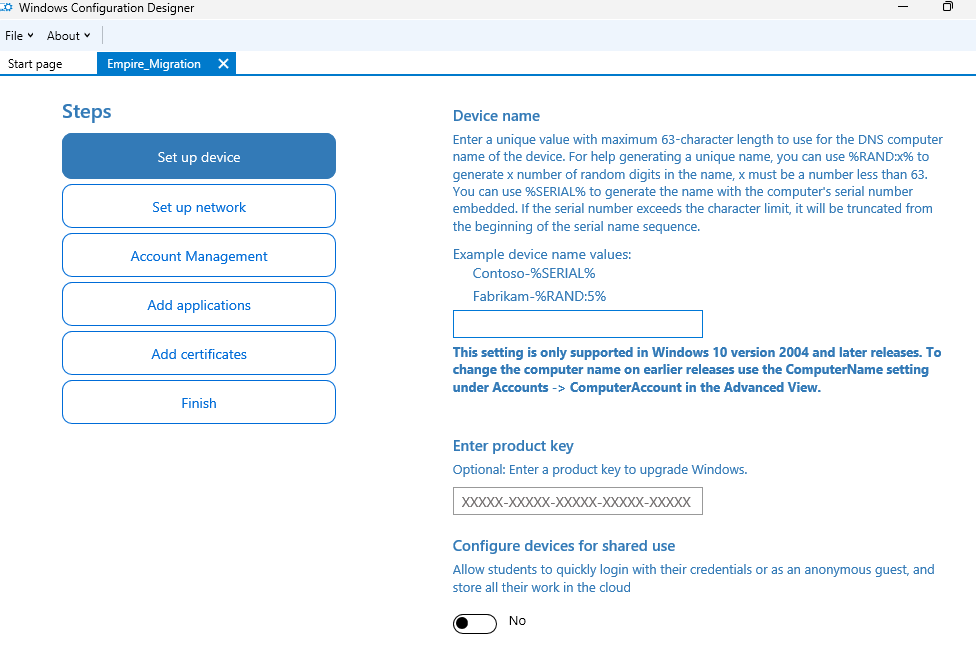
11) Launch Windows Configuration Designer, selecting the "Provision desktop devices" options, choose your device hostname prefix and go ahead and request your juicy Bulk Enrolment Token!
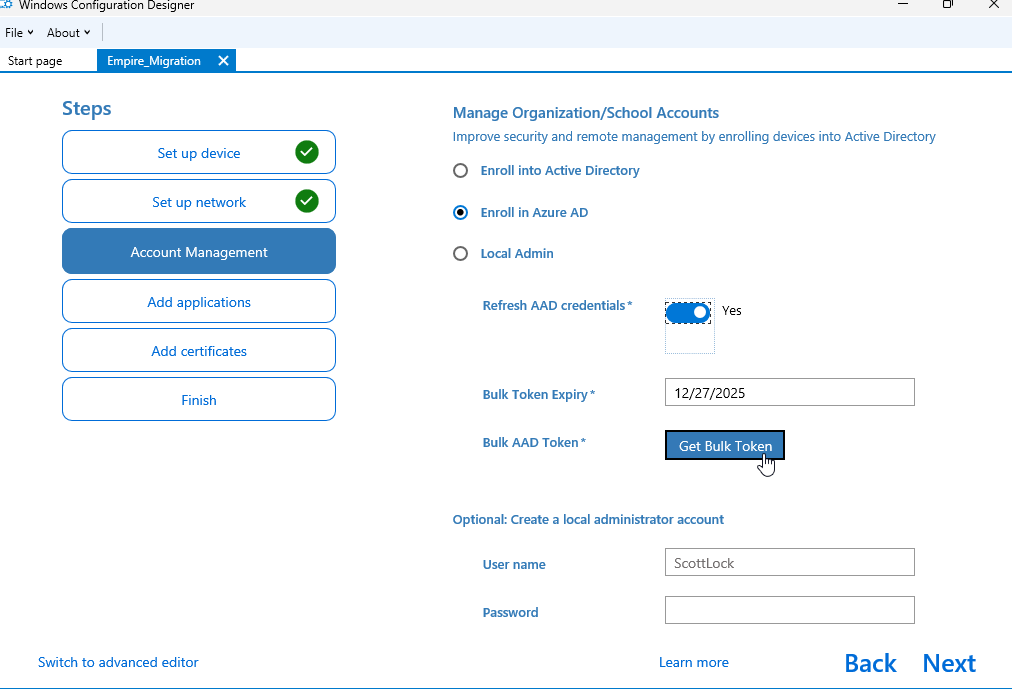
12) Navigate to Entra and ensure you exclude the identity with the prefix "package" from your MFA and Geo-restriction polices - with caution of course, get it approved if needed. You can always restrict the enrolment to whichever IP the devices have the migration initiated from if required for your Conditional Access polices.
13) Once you've created your provisioning package, copy it from the saved directory and paste it straight into the Visual Studio project.
Intune Application Deployment
Now we'll wrap it all together by packaging the solution into an Intune Application and uploading it to Intune, the key here is to make the App a "Required" app for a user group who you will be migrating. This way, the app will appear in Company Portal and allow the user to initiate the process when ready!
14) Launch the IntuneWinAppUtil.exe, within the directory of the migration solution and wrap it all up like so:
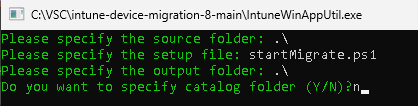
15) Now you shall find a file named "startMigrate.intunewim" - this is what you need to upload to Intune.
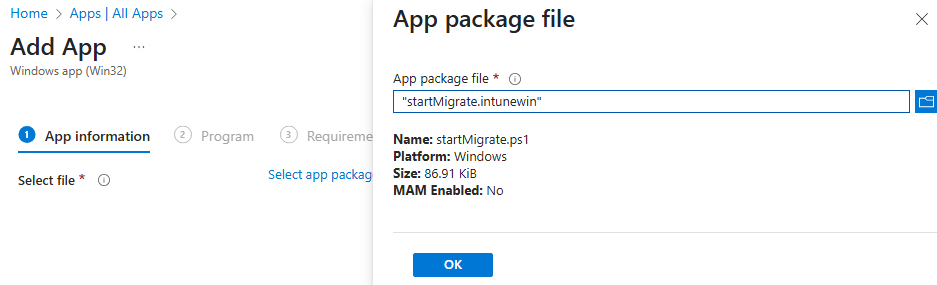
16) Make your way through the steps in Steve's guide, as you can easily paste the required parameters in to make this all work.
The Migration Process
Now the part you've all been waiting for - the end user experience!
Once the app has been uploaded and assigned via Intune, logon as a user and open Company Portal where you should find your migration app.
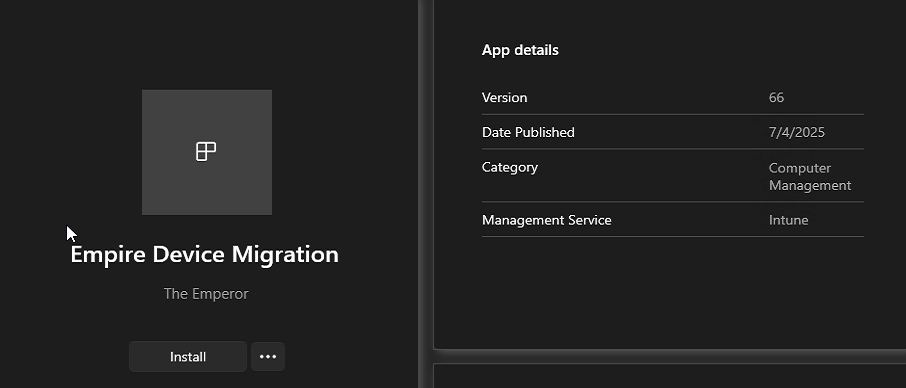
Go ahead and hit install!
You can see below that the "IntuneMigration" folder has been created including all the information and Provisioning Package which you created earlier.
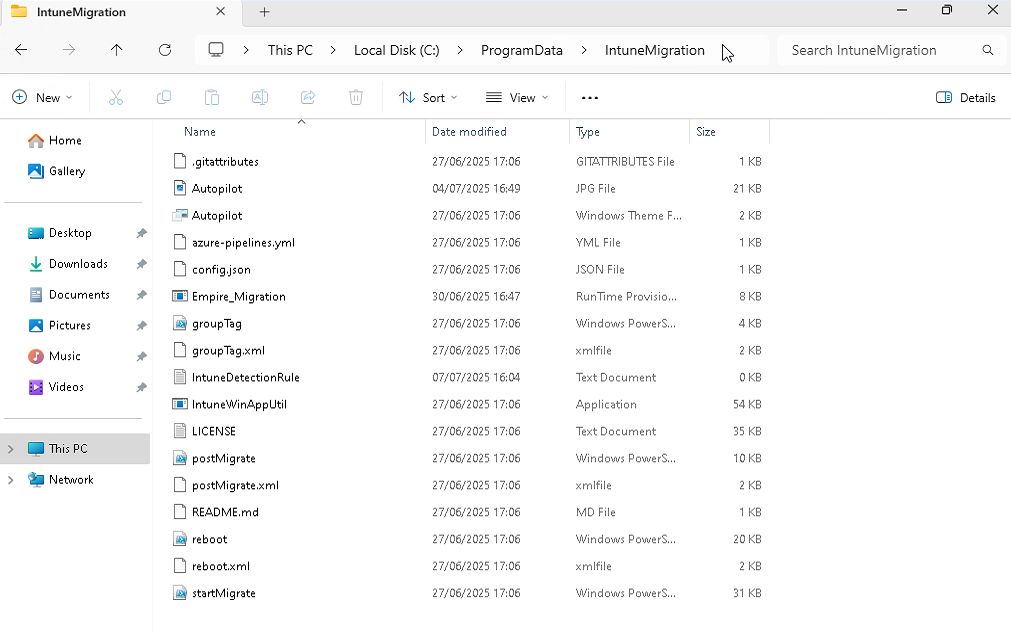
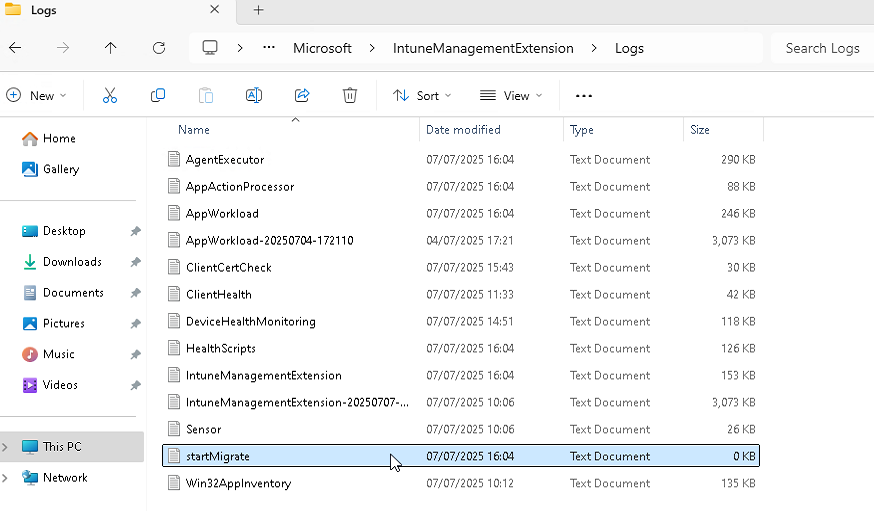
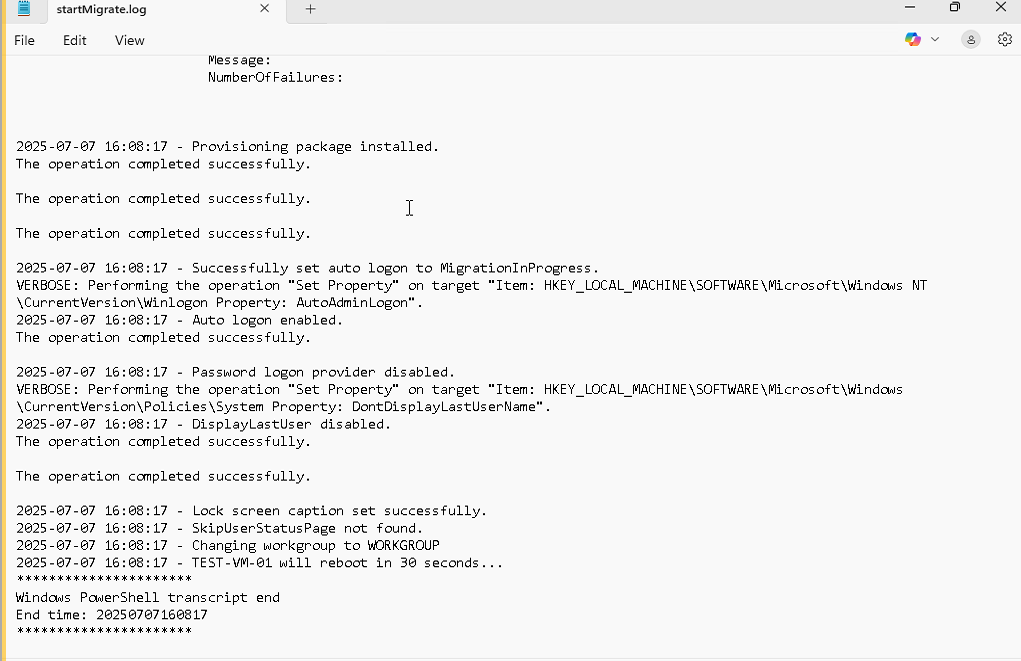
There is also a useful logging file created in the "IntuneManagementExtension" Logs folder called "startMigrate" - this is useful to validate what is happening with the process and if there are any issues. I previously had an issue with authenticating to the destination tenant - this log helped me validate that.
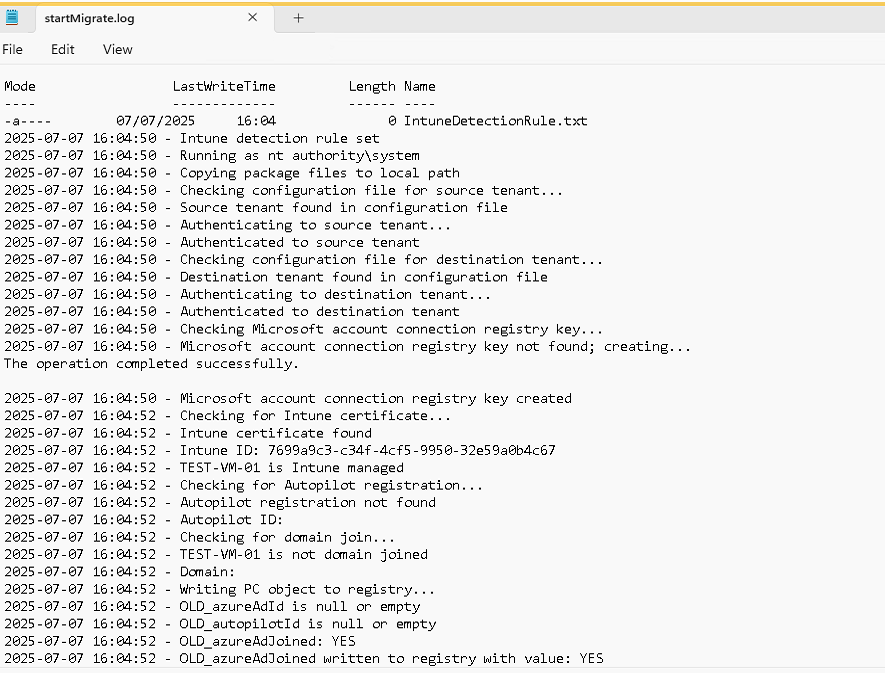
Here you can see within the log file that the detection rule has been set, the source and destination authentication was a success and some useful information on my device TEST-VM-01 with the validation that it is Intune managed.
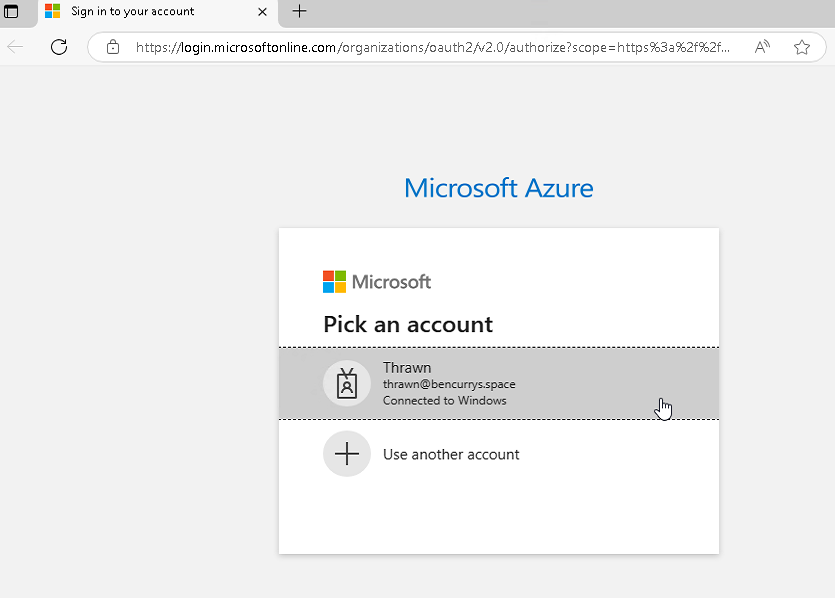
Back to the process now - you will be prompted to confirm your source tenant credentials within the browser - go ahead and do that.
Finally, you can now see within the log file that the final steps are complete and the device is now part of a Workgroup and is about to be rebooted.
After this, let the device reboots continue, you will then be presented with a logon page which welcomes you to your destination tenant - go ahead and login with your destination credentials and just like magic, the device has been migrated between tenants 🤩
Closing Thoughts
Once again, full credit goes to Steve for releasing this solution and making it available on GitHub! This has been a reoccurring roadblock in many tenant migrations I've scoped and delivered in recent years - now we have a tried and tested solution which will become part of the migration toolkit.
See below links for Steve's website and YouTube which includes many other fantastic guides and solutions 💻
Until next time 😎




